Whole-Disk Encryption
Computer
Security Lecture, Dr.
Lawlor
Q: Why bother with encryption? My
laptop is safe--I'm over 6 foot tall and know some Karate.
A: A huge number of
data breaches are caused by laptops left in cabs, bars, and hotel
rooms. Others are caused by careless handling of dead
hardware, or backup disks. Others are caused by
intrigue or an armed assault.
Q: But I password-protect Windows, and
even my BIOS!
A: One screwdriver is
enough to physically pull the drive, and then they can read the
filesystem on any machine they like.
Q: Why isn't it enough to encrypt just
the important files?
A: Sensitive data can
leak to temporary files, hidden, and deleted files. Swap
files, or filesystem slack space, are particularly bad. Some
editors, like Word, are bad about leaving parts of erased data
inside existing files.
Q: OK, I'm sold. I just AES'd my
disk. Why's it so slow?
A: Most good
encryption algorithms, especially Cipher
Block Chain (CBC) style, are sequential--this means you
could only decrypt the disk by starting at the beginning and
working your way through. For a normal disk, you want random
access, so you need to be able to pick up the encryption at any
disk block.
Q: OK, I now AES each disk block
separately. Wait, why are there all these repeating
patterns?
A: You need a
different initialization vector for each disk block. Using
the same IV basically devolves the cipher to electronic codebook
for disk blocks, so the same 512-byte block always produces the
same 512-byte ciphertext. Using a predictable IV, like the
disk block number, still allows a watermarking attack, where somebody carefully crafts a file
with modifications to cancel out your changing IV, revealing a
repeating pattern in the encrypted data. A better scheme is
to make the IV's depend on the key, like ESSIV (encrypted salt-sector initialization vector), although there
are many options.
The old (2.6) linux interface losetup is
vulnerable to this sort of attack, even from my 5-minute C program. Here's the encrypted filesystem
when writing the watermark file to an losetup filesystem:
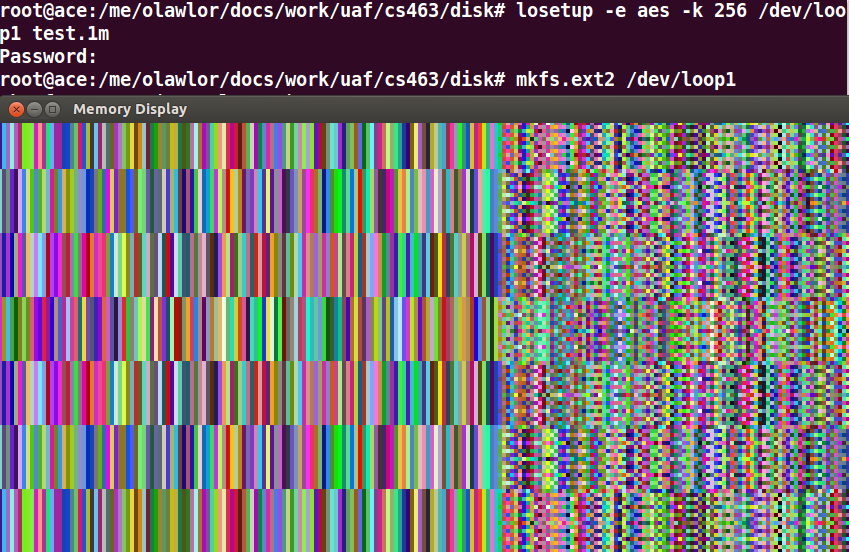
Here's the same file written to a newer
cryptsetup filesystem:
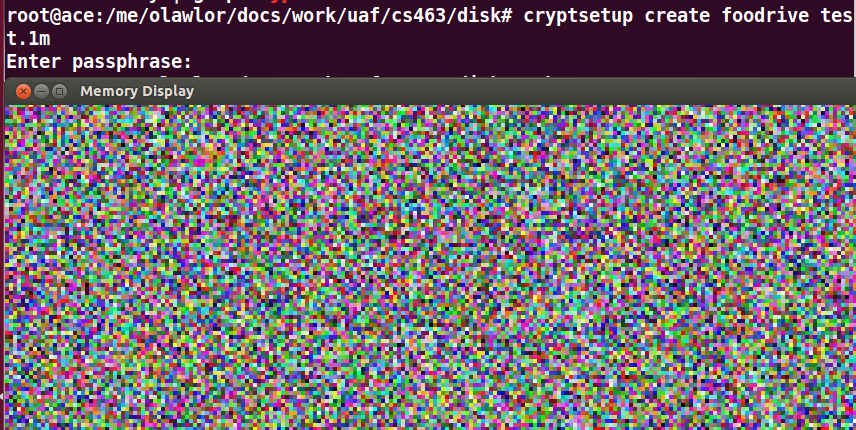
Note the repeating patterns (the
watermark) is gone. See the full command list below.
Q: How do I set this stuff up?
A: The bad news is you basically need to
create an entire new filesystem to get encryption, on most
machines there's no easy way to add encryption to an existing
partition. Definitely back up your data before encrypting
it; I know several smart people that have lost all their files due
to malfunctioning encryption.
On post-XP high end Windows versions (Pro, Enterprise, etc),
Microsoft's full disk encryption is called BitLocker.
On MacOS X, Apple's full disk encryption is called FileVault.
TrueCrypt had an IP battle in 2014 and the
maintainers stopped maintaining it, but there haven't been serious
problems found in the drive encryption itself when
audited (although there is a privilege escalation
vulnerability using DLL
hijacking).
The new and watermark-resistant Linux
way is using dm-crypt;
there is a fancy key manager called LUKS.
Here is the simplest non-LUKS approach (one key) using cryptsetup:
sudo su
swapoff -a
modprobe dm_crypt
dd if=/dev/zero of=test.1m bs=1024k count=1 # create empty file (first time only)
cryptsetup --cipher aes-xts-plain64 --key-size 256 create foodrive test.1m
mkfs.ext2 /dev/mapper/foodrive # create filesystem (first time only)
mkdir tmp
mount /dev/mapper/foodrive tmp
... filesystem is mounted to tmp ...
umount tmp
cryptsetup remove foodrive
In Linux, the old and less secure 2.6 way is using
cryptoloop:
modprobe cryptoloop
modprobe aes
dd if=/dev/zero of=test.1m bs=1024k count=1
losetup -e aes -k 256 /dev/loop5 test.1m
mkfs.ext2 /dev/loop5
mkdir tmp
mount /dev/loop5 tmp
... filesystem is mounted to tmp ...
umount tmp
losetup -d /dev/loop5
Q: I need to let my husband use my
computer, but I don't want to give him the same password.
A: It's probably more
secure to have separate computers, but the standard trick for
multi-user access to a single shared encrypted disk is to have one
"disk key" that is stored in several copies, each one encrypted
using a separate "user key". The standard disk format on
Linux for this is LUKS. You can set this up so any authenticated user can
read the disk, but nobody else can. You could also have an
unencrypted copy of the disk key in a vault or safe deposit box,
for backup.
Q: Help, I forgot my disk key!
A: It sucks to be
you. If you don't have an emergency recovery information
(ERI) file, or a key escrow somewhere, your data is now gone. Hopefully you've got
backups elsewhere!
Q: So if the filesystem is encrypted, even if they have physical access they can't read my files. Cool. They can't write my files either?
A: Not only can they erase your files, there are known "malleability attacks" where if they know enough about how your files are laid out, they can write to selected areas of the filesystem, potentially doing evil stuff like adding a remotely accessible backdoor.
Q: How do I break my adversary's full disk encryption?
- Find their decryption key in their emergency recovery file, or key escrow system. BitLocker allows your active directory domain admin to have key escrow, and a custom Kerberos server could bypass BitLocker on pre-2015 versions of Windows on a domain (MS15-122).
- Bruteforce their decryption key; hashcat has modes for most encrypted filesystems.
- Find the copy of that same data that isn't encrypted, like their backup data, in the swapfile, the email attachment, the thumb drive, the digital camera SD card, etc.
- Backdoor their machine's hardware, BIOS, or (unencrypted) boot partition (a Bootkit), so you can intercept their key as they enter it, or access their data after they've logged in normally.
- Extract the filesystem decryption keys from their machine's RAM (see cold boot attack, DMA attack).



